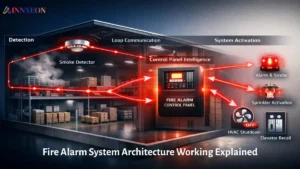
Low-voltage infrastructure has evolved far beyond isolated systems. Modern buildings, industrial facilities, data centres and smart campuses now depend on integrated ELV platforms that unify fire alarms, CCTV networks, access control and other safety and security technologies.
Instead of managing separate hardware, software and cabling systems, engineers are designing converged ELV architectures that improve response speed, reduce cost and increase operational visibility.

This article explores how engineering teams successfully integrated fire alarm, CCTV and access control into a single ELV platform.
You’ll learn the system design approach, communication protocols, hardware standards, interfacing methods and practical lessons gathered from real-world deployments.
Why Integration Became Essential
Just a few years ago, fire alarm systems operated independently from video surveillance and access control. That meant:
- Multiple control rooms and separate monitoring interfaces
- High cabling and installation costs
- Delayed emergency response due to siloed alerts
- Difficulty achieving centralized reporting and compliance
ELV engineers pushed toward unified platforms for 3 major reasons:
- Centralized monitoring and control
One command room or BMS interface now manages all security and life safety systems. - Event-based automation
A single incident (fire, intrusion, forced entry) can trigger automated CCTV views, door actions and alarms. - Cost and cable reduction
IP-based systems allow shared infrastructure over Ethernet, PoE and fiber.
Step-by-Step Integration Strategy
To merge three major systems, fire alarm, CCTV and access control, engineers followed a layered integration approach.
1. Define the Core Objective
The first step was to determine what the integrated platform must deliver:
- Instant alarm-based triggers across subsystems
- Real-time communication with the SCADA/BMS
- Remote monitoring capability
- Scalable architecture for future expansion
- Compliance with fire, safety and data protection standards
2. Select Compatible System Components
Integration is not just wiring. Engineers had to select hardware and software that support open communication, shared protocols and hybrid interfacing.
Fire Alarm Panels:
Brands commonly used include Edwards, Honeywell, Notifier, GST and Bosch, chosen for:
- Addressable loops
- TCP/IP communication modules
- Modbus, BACnet, or RS-485 gateways
CCTV Systems:
Industrial-grade NVRs and IP cameras with:
- ONVIF compliance
- RTSP streaming
- API/SDK-based integration
- PoE support
Access Control Panels:
Devices with:
- Wiegand, RS-485, OSDP, or IP connectivity
- Relay switching capability
- Integration-ready event logs
3. Build a Network-Centric ELV Infrastructure
Instead of segregated cabling, engineers designed a unified structured cabling network using:
- CAT6/CAT6A for IP-based devices
- Fiber optics for backbone distribution
- PoE/PoE+ switches for CCTV and access terminals
- Shielded twisted pair for legacy fire alarm loops
Access control systems and CCTV utilized IP directly, while fire alarm panels interfaced via IP gateways or serial converters.
Network Hierarchy
A typical architecture adopted:
- Core Switch (Fiber Uplink)
- Distribution Switches
- Edge PoE Switches for CCTV and access nodes
- Redundant fire panel gateways
This ensured both isolation and interoperability across subsystems.
4. Establish Communication Protocols and Interfaces
The integration relied on open standards to enable seamless connectivity:
| System | Common Protocols Used |
|---|---|
| Fire Alarm | Modbus TCP/IP, BACnet/IP, RS-485 |
| CCTV | ONVIF, RTSP, API/SDK |
| Access Control | OSDP, Wiegand, IP-based REST/HTTP |
For legacy equipment, engineers used interface relays or dry contact modules to connect events from the fire panel to the access system.
In many deployments, the Building Management System (BMS) acted as the central integration hub.
5. Software-Level Integration
Instead of switching between multiple software tools, everything was centralized into a single monitoring dashboard.
Key options include:
- BMS dashboards (Honeywell EBI, Schneider EcoStruxure, Siemens Desigo)
- PSIM (Physical Security Information Management)
- Custom APIs connected to SCADA
- Central Command & Control Systems
Engineers configured:
- Event automation rules
- Trigger-based camera pop-ups
- Door unlock/lock during alarms
- Incident logging and reports
- Priority-based alerts
6. Event-Based Automation Scenarios
To ensure real-time response, engineers programmed interlinked actions:
Scenario 1: Fire Alarm Trigger
- Fire panel detects smoke on Level 3.
- Command sent to BMS via Modbus.
- CCTV system auto-displays camera feeds for affected zone.
- All magnetic locks release for evacuation.
- Voice evacuation messages begin.
- Fire doors close automatically.
Scenario 2: Forced Entry Detection
- Access control detects a forced door.
- CCTV PTZ camera zooms on location.
- Security room receives instant alert.
- Event logged with timestamp.
Scenario 3: Restricted Area Access
- Unauthorized card used.
- Door remains locked.
- Camera recording begins.
- Email/SMS alert sent to facility manager.
7. Fire Alarm Integration Challenges and Solutions
Integrating fire alarms required careful compliance with NFPA and local codes.
Key challenges engineers faced:
- Ensuring no delay in alarm signaling: Used direct relay contacts for emergency pathways, not just IP triggers.
- Isolation between fire and security networks: Implemented VLAN segmentation and firewall rules.
- Non-compatible legacy hardware: Used protocol converters, relay modules and serial gateways.
- Fail-safe door behavior: During a fire, access doors default to unlocked state.
- UL and Civil Defense approvals: All interfaces complied with local authority standards.
8. CCTV Integration: Practical Approach
Video integration went beyond streaming. Engineers mapped camera FOVs to specific fire zones and access points. Key features included:
- PTZ presets linked to alarm inputs
- Motion-triggered recordings
- Remote mobile app surveillance
- NVR-SCADA communication via HTTP and API
To ensure uptime, they used:
- RAID storage
- Redundant NICs
- Layer-3 VLAN routing
- UPS and dual power sources
9. Access Control Integration: Smart Linking
Access control merged both safety and security needs.
Core setup involved:
- IP controllers compatible with BACnet or Modbus
- Door sensors linked to fire alarm contacts
- PoE-powered card readers and door strikes
- Automatic unlocking for emergency exit routes
Integration ensured:
- Real-time tracking of personnel movement
- Doors auto-release during fire alarms
- Lockdown modes during security breaches
10. Testing and Commissioning
Before handover, engineers conducted multi-system testing:
- Panel-to-panel communication
- Alarm event propagation checks
- CCTV trigger validation
- Access fail-safe operations
- Smoke detector simulation
- Log verification and timestamp sync
- Redundancy check on gateways and switches
Commissioning reports included:
- IP schema
- Wiring diagrams
- Event logic charts
- Equipment mapping
- Panel and BMS integration logs
11. Benefits Observed After Deployment
Once the platform went live, both project teams and end clients witnessed a range of operational advantages.
🔹 Enhanced Situational Awareness
Operators could see live CCTV feeds the moment a fire alarm, intrusion, or manual trigger occurred, without switching screens.
🔹 Faster Emergency Response
Event automation removed manual delays in alerting, unlocking doors and dispatching teams.
🔹 Cost Reduction
Unified cabling, shared servers and central software eliminated redundant infrastructure.
🔹 Compliance and Reporting
Digital logs simplified audits for safety authorities, civil defense and insurers.
🔹 Scalability
The entire setup was future-ready for:
- PA/BGM systems
- Intrusion alarms
- Lighting control
- IoT sensors
- Smart parking and visitor management
12. Best Practices from Real Deployments
Based on field experience, engineers highlighted these lessons:
- Choose open-protocol systems only
Proprietary platforms increase cost and limit expansion. - Involve IT teams early
ELV is now an IP-driven ecosystem, not a standalone discipline. - Design VLANs for each subsystem
Helps maintain security and bandwidth control. - Always implement dual communication paths
Fire alarm > dry contact + TCP/IP for redundancy. - Document integration logic clearly
Makes maintenance and troubleshooting easier. - Use PoE+ switches for access devices
Eliminates separate power adapters. - Plan for future analytics and AI
Integrated CCTV feeds can later support video analytics and behavior detection.
13. Common Mistakes to Avoid
Even experienced integrators sometimes overlook these points:
- Mixing fire alarm loops with network cabling
- Using DVRs instead of NVRs for IP cameras
- Forgetting fail-safe door unlocking logic
- Ignoring latency between protocols
- Not using surge protection for edge devices
- Missing BMS integration documentation
- Overloading switches without QoS rules
14. The Future of Integrated ELV Platforms
Today’s integration of three systems is only the beginning. Large projects are now adding:
- AI video analytics
- Mass notification systems
- Visitor and crowd management
- IoT-based smoke sensors
- Digital twin dashboards
- Cloud-based access credentials
Edge computing, 5G, and cybersecurity protocols will drive the next generation of building safety platforms.
Note: Integrating fire alarm, CCTV and access control into a single ELV platform is no longer just a premium option, it’s becoming the default expectation in industrial, commercial and smart infrastructure projects. For engineers and system integrators, the competitive advantage lies in mastering:
- IP-based architectures
- Cross-system communication standards
- Fail-safe event automation
- Compliance with life safety codes
- Scalable infrastructure design
A well-executed integration not only improves safety and response time but also streamlines long-term maintenance, reduces CAPEX/OPEX costs and prepares the facility for future expansion.
Read Also: Fire Alarm Safety System Engineering Insights for Oil & Gas Refineries
Read Also: Fire Alarm System Design for Large-Scale Manufacturing Plants